Finally, Back to the blog !!
In today’s blog we are going to see AWS Security Reference architecture (In short SRA). Definitely I’m not reinventing the wheel 🙂 But trying to make wheel accessible as much as possible . I get you enough of philosophy , right ? Ok, Lets jump IN
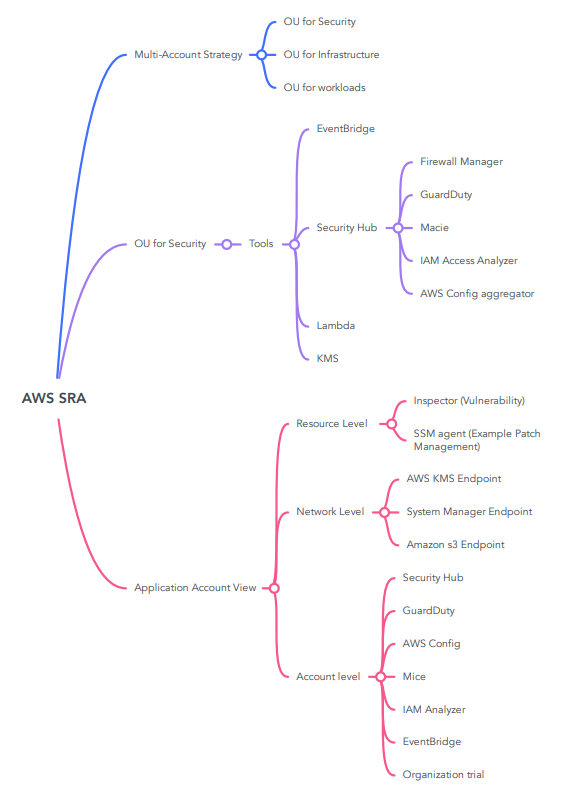
AWS recommends to have a multi-account strategy for implementation of security at scale. What does it mean ? AWS helps customer to organize their accounts using OU , OU’s . we use it for the security as well. Example, Lets say Customer A has 100+ Accounts in their environment. we create Root Management account. And we create OU’s .
- One for Security
- One for Infrastructure (Example, VPC)
- One for Shared services
- One for the Actual workload (This can be more depending on the customer)
Let’s get one level down with security. When implementing security we need to be aware of
- What are the security services in AWS? why we need it?
- Where can it be implemented?
- How can it be implemented?
In this blog, I will be answering why? what ? where ? of Cloud Security Posture Management
Why we need CSPM?
- Compliance reasons
- Make sure resources are created with defined configuration and monitored against those configuration
What are the services that can be used to implement?
- AWS Control Tower, It not only helps with organizing the OU’s and Landing page But it also helps in managing security policies using Guardrails.
- Guardrails are of two types
- Preventive (Example Service Control Policies , Implemented at organization level)
- Detective (using AWS config rules)
- AWS Security HUB, you get the visibility of non-compliance across all the accounts. For implementation, the recommendation is to delegate the administration to the security account and add all the member accounts to the master account.
- AWS config, Service used for defining the compliance policies . To ease AWS Config implementation, conformance packs can be used . Rules can be deployed against an account, region or across an organization.
Where are the services implemented?
- Service Control Policies at the Organization level
- AWS config rules depending on the customer needs (Can be account, organization, against specific resources)
- AWS security HUB at the delegated account (within the Security – OU)
In coming weeks , Lets talk about Integrating IAM (CIEM) , Data Protection to the list.




Leave a comment