Today ! Lets secure the EKS based on EKS Best Practice
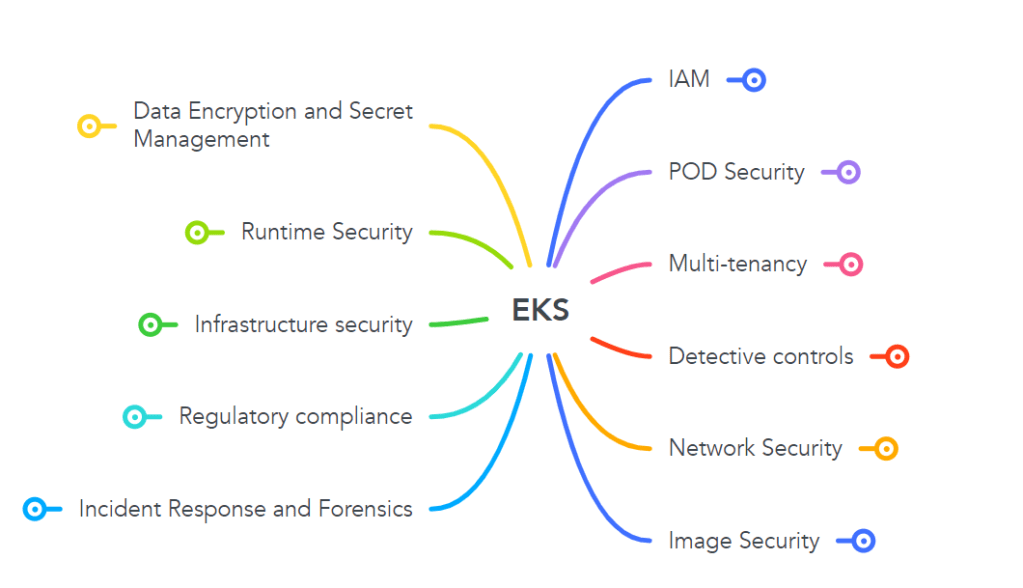
As in any service of AWS, Security starts with IAM. Access is provided to only required resource/entity . Always follow the Least Privilege Model. To keep it simple, Authentication is done from IAM Service, Authorization is done by RBAC of the kubernetes. It is also possible to assign IAM role to the service accounts of the PODs (Nice Video to illustrate the steps)
POD Security, you can secure POD’s using the Policy as a Code (Example OPA) or using POD Security Standards. you can define standards on how you want to deploy the PODs . you can define controls like enforce, Audit , warn if there is a violation.
Multi-tenancy, This can be implemented in two ways soft multi-tenancy , hard multi-tenancy. Soft tenancy via Namespace, Roles and Network policies. It is called soft because pods would still be using the same node resources. Hard tenancy can be implemented using Node affinity , Taint/Toleration
Detective Controls, There are two types of logging in EKS. Audit logs , is send to the CloudWatch . Control planes logs can also be enabled and forwarded to the CloudWatch. API logs can be forwarded to the CloudTrail. This can be a base for understanding unusual behaviour in the environment.
Network Security, It can be implemented using Network Policies. There are numerous third party vendors that can facilitate the implementation (Example Calico) . POD IP’s are ephemeral , so it is helpful to have POD information in VPC logs to investigate incidents. Security Groups can also be used to implemented for the POD communication (Nice Article). It is also important enable encryption between the communication (Example between POD to POD)
Data Encryption and Secret Management, As a thumb rule it is recommended to encrypt data during rest, transit and in-use. By default, secrets are stored in Etcd But it is possible to manage it using the external stores like Hasicorp vault.
Runtime Security, There are numerous third party vendors to implement runtime security in the market. To name few Sysdig , Prisma Cloud.
Infrastructure Security, Amazon Inspector can be used to check the vulnerability in the nodes hosting the PODs. Compliance check can be performed by tools like Kube-bench (Aqua security)
Regulatory compliance, Policy as a code/ OPA can be used to govern the specification/compliance of the resources
Incident Response and Forensics, Important to have game plan in case of an incident. Some of steps are isolating the containers, Revoking the comprised credentials , cordon the nodes.




Leave a comment