Why it is important ?
Based on recent report from CloudFlare there was has been an increase in the API traffic from 52 to 54% between Feb 2021 to Dec 2021.
Similarly there is growth rate of 20% across this period. Highest compared to any other types of internet traffic.
Based on Gartner report, By 2022, API abuses will move from an infrequent to the most frequent attack vector, resulting in data breaches for enterprise web applications.
Based on recent wallarm report, there have been 186 Vulnerabilities reported in Q2 compared to 50 in Q1 of 2022.
Understanding API
API uses
- Client/Server architecture.
- HTTP protocol
Generally, API Gateway is used to manage the API requests. Also act as a single entry point for the API requests.
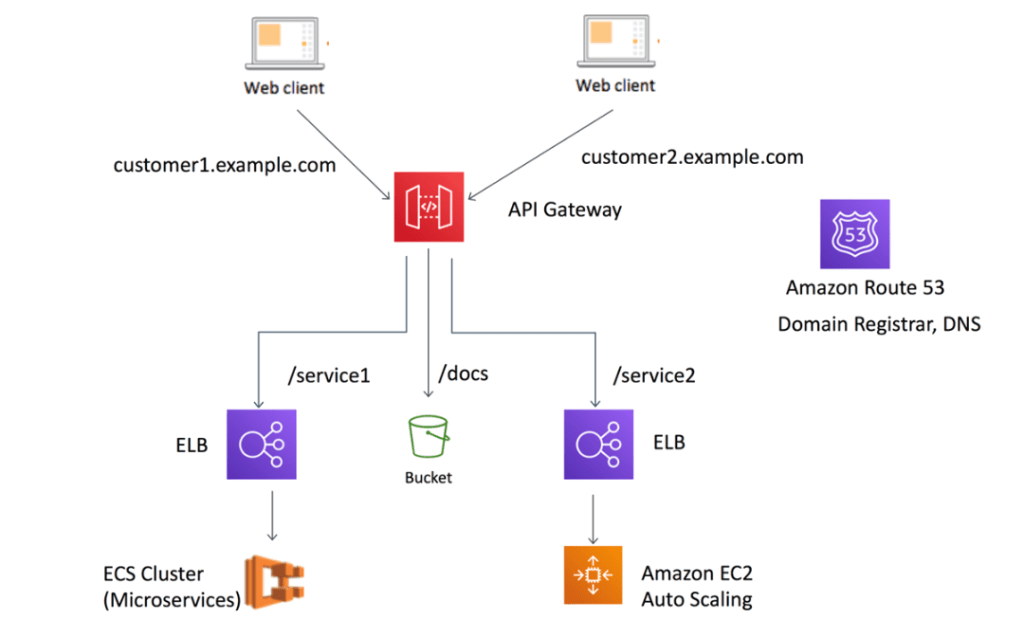
API consumers does not access the backend directly, rather they access the resources using the endpoints. There are two major API types
- RESTful API
- GraphQL
RESTful API
REST defines 6 constraints
- Uniform interface , Interface has to be same irrespective of consumer device (Example mobile, browser)
- Client/server, It should have client/server architecture
- Stateless, Communication should be stateless
- Cacheable, Response should indicate whether is it cacheable or not
- Layered system, REST allows you to use a layered system architecture where you deploy the APIs on server A, and store data on server B and authenticate requests in Server C
- Code on demand (Optional), free to send executable code
REST API request has a Method, Endpoint, HTTP version, headers . REST API response has a HTTP version, response code, cache-control, body (with the data).
In REST API, consumer needs to filter out the data.
GraphQL
It is a query language for API. Data is stored in graph data structure. Customer would be able to request exactly based on need. Nothing more like REST API
OWASP API Top 10
Now with the knowledge on components , Lets see the OWASP API Top 10
The last updated version is from 2019 , I don’t know reason why? If someone knows Please comment. Either way let’s get to Top 10 list They are
API1:2019 Broken Object Level Authorization , Generally called as BOLA . Occurs when provider allows consumer to access the resource without verifying the authorization.
API2:2019 Broken User Authentication, Occurs when user authentication is not implement and implemented wrongly by the provider.
API3:2019 Excessive Data Exposure, Occurs when excessive data is returned than the actual requested data.
API4:2019 Lack of Resources and Rate Limiting, Occurs when there is no resource to respond to the request , this can occur when there is no rate limiting (Restricting the number of request then can be made by a consumer within a specific duration)
API5:2019 Broken Function-Level Authorization, Occurs when users from a function able to access data from other function without authorization.
API6:2019 Mass Assignment, when user is able to update the parameters which he shouldn’t be able to. This occurs when provider does not verify the input provided by the consumer.
API7:2019 Security Misconfiguration, General misconfiguration by the providers that can cause attackers to exploit.
API8:2019 Injection, Just like Web App Injection. If the provider does not verify the code which can result SQL or other Injection
API9:2019 Improper Assets Management, Occurs when Non-production API which are yet to be secured Or depreciated API that contains vulnerability is closed. This occurs when there is no inventory for API in the environment or unavailability of the API lifecycle process.
API10:2019 Insufficient Logging and Monitoring, when there is no sufficient logging or monitoring . Incident Management should be integrated to monitoring/alerting.
In the Market, There are vendors like salt security, Noname security, Imperva (Cloudvector), Traceable (To name few) to secure the API.




Leave a comment