Azure security updates
- Azure Bastion now supports Microsoft Entra ID authentication for SSH connections in the portal (Link)
AWS security updates
- Customers can now access and manage their Network Firewalls privately, without going through the public internet (Link)
- Customer can create and manage your resource shares from within your Amazon Virtual Private Cloud (VPC) without traversing the public internet (Link)
News from Security World
- Google Confirms CVE-2024-32896 Exploited in the Wild, Releases Android Security Patch (Link)
- Group-IB discovered the Ajina.Banker malware is a major cyber threat in the Central Asia region, disguising itself as legitimate apps to steal banking information and intercept 2FA messages (Link)
- GitLab patches critical flaw (CVE-2024-6678) allowing unauthorized pipeline job execution (Link)
- PoC Exploit for Typosquatting in GitHub Actions (Link)
- Operant AI Lands $10M Investment to Boost Runtime Protection for Cloud and AI (Link)
AI Security
Last news link is to good Segway into the next topic AI Security. we all agree AI is the future but the future will be chaos if AI is not implemented security.
If you have been tracking my blog, Earlier I talked out How to build AI Security and things to consider in the link and in week 12 i talked about what is prompt injection and how it can be mitigated in the link
In today’s article , Lets try to understand scoping of AI . To keep it simple, Application can be run in VM, Kubernetes , App service (To name few)
Similarly AI can be used directly Just like ChatGPT , Or AI Model can be used by SAAS application that you use or you can use the Models that are used by ChatGPT in your application or you can finish tune the Models before using in your application (This doesn’t touch the data) or you can start all the way from the scratch by starting with the data , Meaning you create data and create models and then use those models in your application.
As you can see the responsibility differs as you left to shift (Data -> App). The more you go to the left the more the responsibility in security.
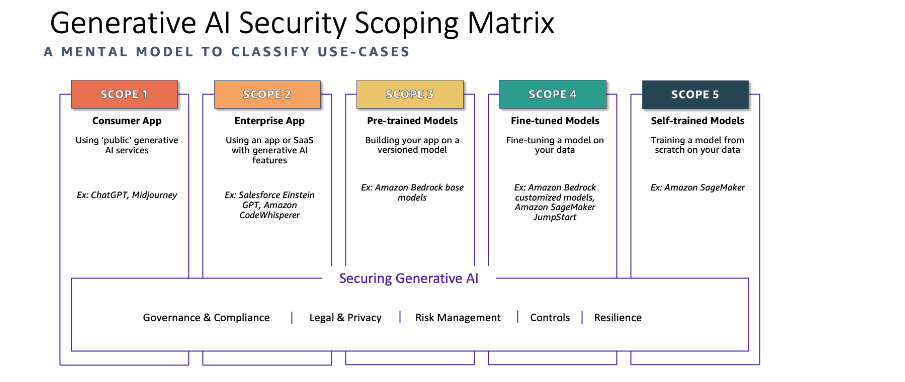
Courtesy AWS Blog (For the snip)
So , Next time when someone talks about AI security. Let’s scope it 🙂




Leave a comment