-
 Continue reading →: Automation in AWS
Continue reading →: Automation in AWSA couple of weeks ago, we saw, How to use Azure service to automate based on the events. If you have not seen it, here is the link. Let’s see how you can automate it in AWS. In AWS, there are many different ways to automate, But one critical service is…
-
Continue reading →: API Security
Why it is important ? Based on recent report from CloudFlare there was has been an increase in the API traffic from 52 to 54% between Feb 2021 to Dec 2021. Similarly there is growth rate of 20% across this period. Highest compared to any other types of internet traffic.…
-
Continue reading →: Cloud Security Weekly News – Week 35
AWS Security AWS is working on migration to NIST 800-53 Revision 5 (Link) currently AWS meets Rev 4. Now its possible to be up to date with AWS security hub announcements via SNS (Link) AWS Firewall Manager now supports AWS managed rules for AWS Network Firewall (Link) AWS WAF Fraud…
-
 Continue reading →: Cloud Security Weekly News – Week 34
Continue reading →: Cloud Security Weekly News – Week 34AWS Security AWS config supports 20 new resource types . Why it is important ? Now you can monitor the configuration of newly added resource types there by maintaining governance AWS CyberVadis report now available for due diligence on third-party suppliers CIS Benchmark CIS benchmark is available for Bottlerocket. Bottlerocket,…
-
 Continue reading →: Automating Deployment of Security Agents – Logic App
Continue reading →: Automating Deployment of Security Agents – Logic AppIn today’s blog let’s see how to deploy security agents in Azure automatically using the Logic Apps Pre-requisites Logic App Event Grid Automation Account/Runbook Flow Diagram Flow Event Grid can be used to deliver events to the subscriber. In this case , you can deliver events from subscription or resource…
-
 Continue reading →: Cloud Security Weekly News – Week 33
Continue reading →: Cloud Security Weekly News – Week 33I’m starting a weekly blog (every Wednesday) bringing cloud security news Why now? Being a security consultant , I struggle to go through different sites/blogs to understand the latest/greatest in the cloud security domain. This effort is cover the void and help my fellow security consultants. Azure Security Sentinel Azure…
-
 Continue reading →: Cloud Native Security – Part 2
Continue reading →: Cloud Native Security – Part 2It took a while to get back , But I hope I make it worthwhile for the wait 🙂 This week we will read about how to secure resource during runtime and obtain Security Assurance in our environment. Runtime Just like previous phases, Develop, Distribute and Deploy. It is crucial…
-
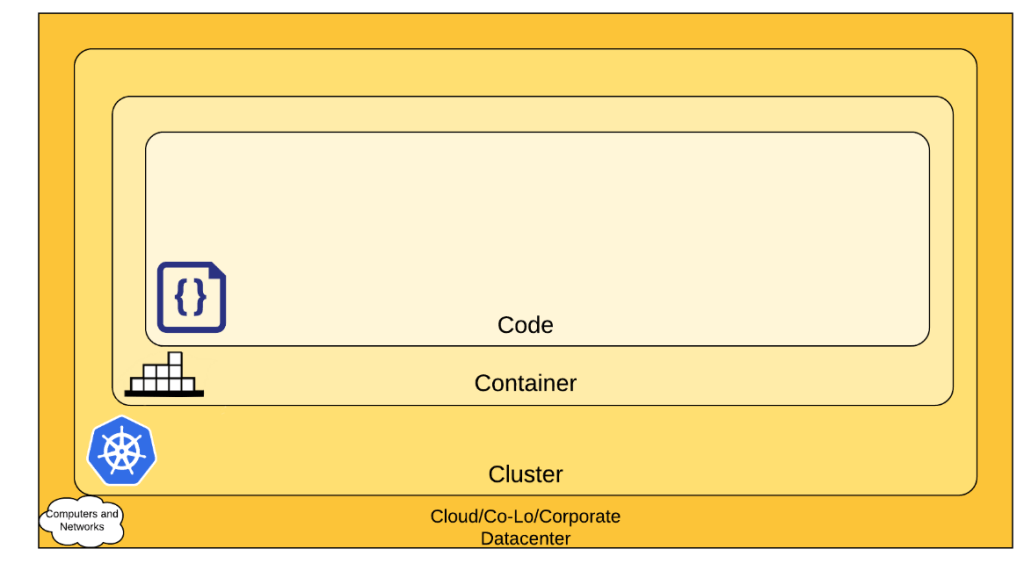
 Continue reading →: Cloud Native Security
Continue reading →: Cloud Native SecurityCNCF published v2 to give The Organization’s a better understanding of Cloud Native Security (CNS) Provides factors to consider while implementing CNS In this blog, I’ll share insight into the details. Why do we need a different view with Cloud Native security? As workload can run anywhere (on-prem, cloud), traditional perimeter security is…
-
Continue reading →: Securing – EKS
Today ! Lets secure the EKS based on EKS Best Practice As in any service of AWS, Security starts with IAM. Access is provided to only required resource/entity . Always follow the Least Privilege Model. To keep it simple, Authentication is done from IAM Service, Authorization is done by RBAC…
Hello,
I’m Ara
Welcome to Cloud Security Blog, my corner of the internet dedicated to Cloud and AI Security .
Let’s connect
Join the fun!
Stay updated with our latest tutorials and ideas by joining our newsletter.